How secure are your medical images? If you don't know the answer, you'd better find out. A recent search found that more than 700 DICOM medical image servers worldwide were fully open to outside computers that could be used to steal data, according to research presented at this month's ECR 2015 in Vienna.
After performing a global search of all Internet protocol (IP) addresses, Oleg Pianykh, PhD, of Harvard Medical School in Boston found nearly 2,800 DICOM servers that did not have firewall protection. Of these unprotected DICOM servers, 25% were accepting external DICOM "handshakes" (i.e., DICOM connection requests), indicating the servers were fully open to DICOM communications with outside computers.
"Over 20 years after the [the implementation of digital medicine], patient data is still unsecured," he said. "If you think that your hospital has not been hacked yet, then you probably just do not know about it."
More frequent breaches
Clinical security breaches can have a significant effect on healthcare institutions and patients, and seem to be happening more frequently, Pianykh said. In an effort to explore the current status of clinical security, he designed a probing application that would determine whether an arbitrary computer (using its remote IP address) would support the DICOM clinical data networking protocol.
Utilizing some multicore programming and a highly parallel Amazon server cluster, the application was able to scan the entire global IP space (4 billion IP addresses) in a month. After identifying the IP addresses that accepted the DICOM communication requests, he then used geolocation techniques to identify the unprotected IP addresses and pinpoint their coordinates and providers/owners.
The search discovered 2,774 unprotected IP addresses corresponding to DICOM servers worldwide. Of these, 719 IP addresses were fully open to receiving DICOM communication, representing a significant security risk.
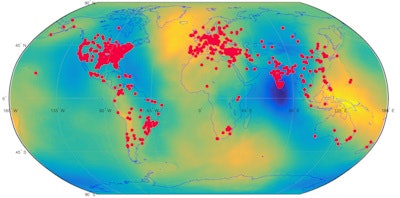 Global map of open DICOM servers. Image courtesy of Oleg Pianykh, PhD.
Global map of open DICOM servers. Image courtesy of Oleg Pianykh, PhD.Countries with the highest ratio of open DICOM servers to all detected DICOM servers:
- Iran: 34/40 (85%)
- Thailand: 10/14 (71%)
- Spain: 11/23 (48%)
- Argentina: 6/13 (46%)
- Russia: 8/18 (44%)
- Brazil: 51/118 (43%)
- Germany: 9/22 (41%)
- Bolivia: 4/10 (40%)
- Australia: 12/32 (38%)
- Turkey: 49/143 (34%)
- Taiwan: 14/41 (34%)
- Poland: 4/12 (33%)
- Japan: 3/11 (27%)
- Chile: 7/27 (26%)
- U.S.: 346/1,335 (26%)
- China: 11/43 (26%)
- Canada: 13/52 (25%)
- Philippines: 6/24 (25%)
- Mexico: 14/57 (25%)
- Hungary: 4/20 (25%)
These DICOM servers may or may not be PACS servers, but their specific role ultimately doesn't matter as much, Pianykh told AuntMinnieEurope.com.
"Most importantly, they are medical image servers -- the ones keeping patient medical data," he said. "And if one gains outside access to them, this becomes a serious breach in clinical security."
For instance, the DICOM server could also be a non-PACS server, such as a clinical workstation with server-like capabilities or some auxiliary clinical division server.
"It may be a little server in an imaging center where they store data before sending it overnight to the central PACS archive," he said. "Still, if it runs DICOM, it is used for medical imaging. And if it's not protected, it's a serious problem."
Pianykh has some simple advice for those institutions seeking to improve the security of their DICOM servers: start taking it seriously.
"It has been assumed for a long time that no one will hack hospitals, but clearly this is a very erroneous approach," Pianykh said. "One can think about many scenarios when the knowledge about someone's medical records can be used to control politics, stock shares, or personal lives. And, unlike a stolen credit card, someone's health cannot be easily 'cancelled' or 'replaced.' "



















